Demystifying the Darkness: Your Guide to Unmasking Dark Web Operations with OSINT
Operation Cookie Monster: Takedown of Genesis Market
On April 5, 2023, the FBI and Dutch National Police announced the takedown of Genesis Market, one of the largest dark web marketplaces. The operation, dubbed “Operation Cookie Monster,” resulted in the arrest of 119 people and the seizure of over $1 million in cryptocurrency.
Genesis Market was a major player in the dark web drug trade. It offered a wide variety of drugs, including cocaine, heroin, and MDMA, for sale. The marketplace also had a reputation for being a safe and reliable place to buy drugs.
The FBI and Dutch National Police began investigating Genesis Market in 2022. They used a variety of techniques to gather intelligence on the marketplace, including undercover operations and data analysis.
In March 2023, the FBI and Dutch National Police executed a series of raids on Genesis Market servers located in the Netherlands. They also arrested the marketplace’s administrators and several of its vendors.
The takedown of Genesis Market is a significant victory for law enforcement. It sends a message to dark web criminals that they are not beyond the reach of the law.
How OSINT Tools Helped Take Down Genesis Market
OSINT (open-source intelligence) tools played a key role in the takedown of Genesis Market. Investigators used these tools to:
- Identify Genesis Market as a major player in the dark web drug trade
- Gather information about the marketplace’s administrators and vendors
- Track the movement of drugs and other illicit goods
- Identify the individuals behind the marketplace
Identifying Dark Websites Using Technical Vulnerabilities
While not considered OSINT, there are instances when technical vulnerabilities can be exploited to identify the true IP address of a dark website. These vulnerabilities may exist in the software itself or be due to misconfigurations.
One common technique is to use pen-testing tools, such as Burp Suite, to induce error messages containing the site’s true IP address. This technique relies on the fact that many dark website operators do not properly handle errors, which can lead to information leakage.
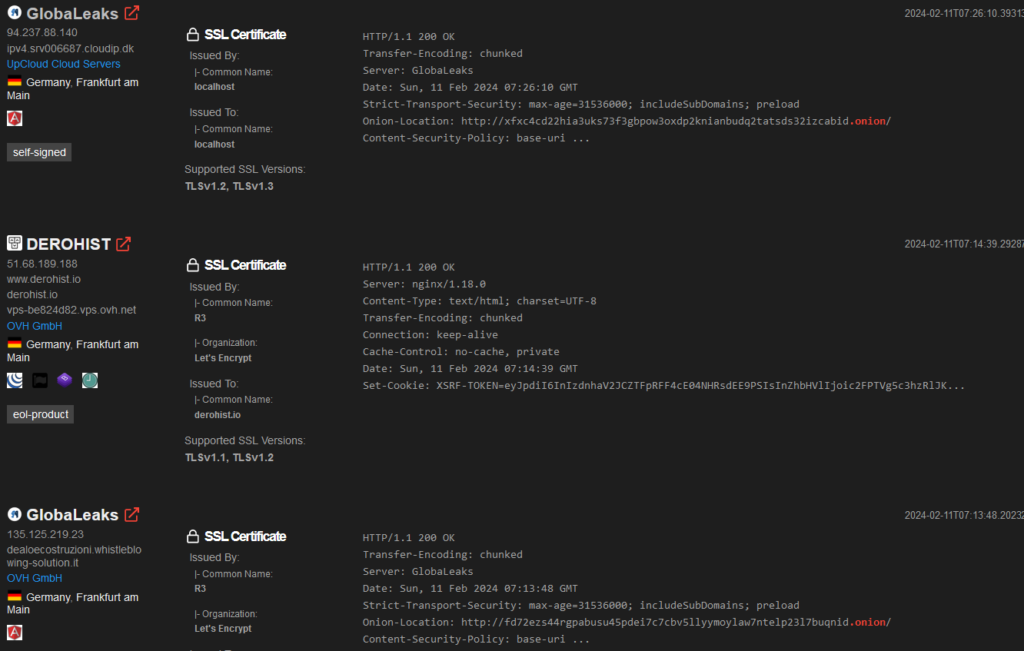
Another technique is to look for SSL certificates or SSH keys that are associated with the dark website. These certificates and keys can be tied to the website’s true IP address using services like Shodan or Censys.
It is important to note that these techniques are uncommon and rarely utilized. This is because they require a high level of technical expertise and are not always reliable. However, they can be a valuable tool for investigators who are trying to identify the true IP address of a dark website.
Cryptocurrency Tracing on the Dark Web
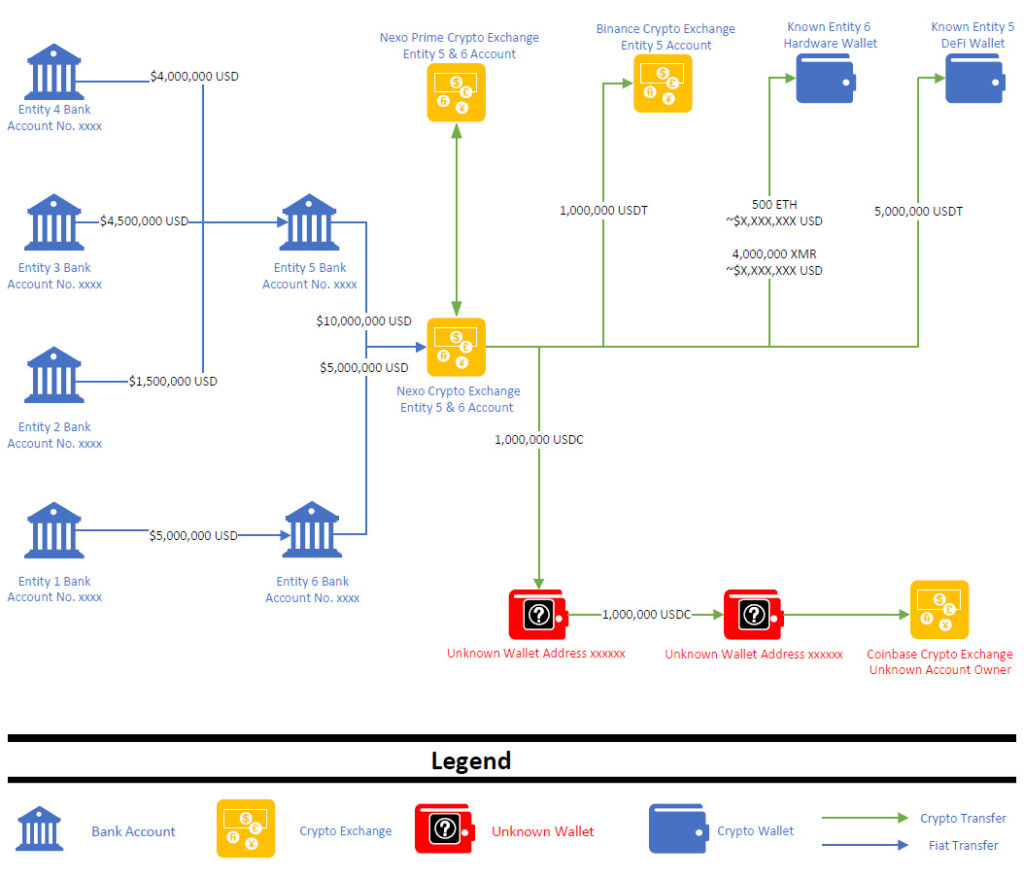
The exchange of cryptocurrencies for illegal goods and services is a common practice on the dark web. The nature of these transactions presents an opportunity to identify parties involved by employing blockchain analysis tools.
Traditional banking requires personal identification to comply with anti-money laundering (AML) and know your customer (KYC) regulations, which prevent anonymous account creation. These regulations require customers to provide government-issued IDs to verify their identities. Many countries have extended similar requirements to cryptocurrency exchanges, demanding them to uphold AML/KYC standards.
Blockchain analysis tools have been developed to link cryptocurrency addresses to specific exchanges like Coinbase or Binance. When a cryptocurrency address is associated with an exchange, law enforcement and financial investigators, with the necessary legal backing, can request the exchange to disclose the identity of the account holder.
While historically the cost of blockchain analysis services was prohibitive for individual use, the landscape has changed with the introduction of platforms like Breadcrumbs (https://www.breadcrumbs.app/). Breadcrumbs offers these services at more accessible prices, including a free tier, democratizing the tools needed for tracing cryptocurrency transactions.
Understanding Favicon Hashing: A Novel Search Technique to Identify Dark Web Sites
In the ever-expanding realm of cybersecurity and digital forensics, professionals are constantly developing new methods to track and trace digital fingerprints across the web. One such innovative technique involves the use of favicon hashing to identify and search for web entities. This blog post delves into the intricacies of favicon hashing and its applications in the field of cybersecurity.
What is a Favicon?
A favicon, short for “favorite icon,” is a small graphic representing a website or webpage, typically displayed in the address bar of a browser tab or next to the site name in a list of bookmarks. Favicons are designed to give a visual identity to a website, making it easier for users to recognize and navigate.
The Rise of Favicon Hashing
Favicon hashing has emerged as a powerful technique for cybersecurity experts. It involves creating a unique digital fingerprint for a website based on its favicon. This is achieved by applying a cryptographic hash function to the favicon file, generating a fixed-size string of characters that uniquely identifies that particular image.
How Favicon Hashing Works
The process of favicon hashing is relatively straightforward:
- The favicon file is retrieved from a website.
- A hash function (e.g., MD5, SHA-1, SHA-256) is applied to the favicon’s data.
- The resulting hash value is a unique representation of the favicon.
Applications of Favicon Hashing
Favicon hashing can be used for several purposes:
- Cybersecurity Investigations:
- Hash values can be used to search databases of known malicious websites. If a favicon’s hash matches one in the database, it can be a red flag for security professionals.
- Digital Forensics:
- Investigators can use favicon hashes to find connections between different websites, which may be owned or operated by the same entity.
- Web Crawling and Indexing:
- Search engines or other web services can use favicon hashes to more efficiently index and categorize websites.
Benefits and Limitations
The primary benefit of favicon hashing is that it offers a quick and efficient way to identify and compare websites without the need for complex image recognition software. However, this technique has limitations. Favicons can be changed easily by website owners, which means the hash value will also change, potentially evading detection.

Understanding Favicon Hashing: A Novel Search Technique
In the ever-expanding realm of cybersecurity and digital forensics, professionals are constantly developing new methods to track and trace digital fingerprints across the web. One such innovative technique involves the use of favicon hashing to identify and search for web entities. This blog post delves into the intricacies of favicon hashing and its applications in the field of cybersecurity.
What is a Favicon?
A favicon, short for “favorite icon,” is a small graphic representing a website or webpage, typically displayed in the address bar of a browser tab or next to the site name in a list of bookmarks. Favicons are designed to give a visual identity to a website, making it easier for users to recognize and navigate.
The Rise of Favicon Hashing
Favicon hashing has emerged as a powerful technique for cybersecurity experts. It involves creating a unique digital fingerprint for a website based on its favicon. This is achieved by applying a cryptographic hash function to the favicon file, generating a fixed-size string of characters that uniquely identifies that particular image.
How Favicon Hashing Works
The process of favicon hashing is relatively straightforward:
- The favicon file is retrieved from a website.
- A hash function (e.g., MD5, SHA-1, SHA-256) is applied to the favicon’s data.
- The resulting hash value is a unique representation of the favicon.
Applications of Favicon Hashing
Favicon hashing can be used for several purposes:
- Cybersecurity Investigations:
- Hash values can be used to search databases of known malicious websites. If a favicon’s hash matches one in the database, it can be a red flag for security professionals.
- Digital Forensics:
- Investigators can use favicon hashes to find connections between different websites, which may be owned or operated by the same entity.
- Web Crawling and Indexing:
- Search engines or other web services can use favicon hashes to more efficiently index and categorize websites.
Benefits and Limitations
The primary benefit of favicon hashing is that it offers a quick and efficient way to identify and compare websites without the need for complex image recognition software. However, this technique has limitations. Favicons can be changed easily by website owners, which means the hash value will also change, potentially evading detection.

Revealing the Hidden Antagonists of the Dark Web
Envision managing a mobile food venture that must frequently relocate due to a municipal regulation that prohibits setting up in the same location more than twice a month. To cultivate customer loyalty and inform potential patrons of your daily whereabouts, you’d likely encourage them to connect with your brand on social media platforms like Facebook, follow your updates on Twitter, or check your website for location announcements. This scenario mirrors the operational challenges faced within the dark web’s volatile environment.
The dark web’s allure of anonymity is counterbalanced by its lack of stability and security. Prominent marketplaces such as Silk Road, AlphaBay, Hansa, Wall Street, and Genesis have all been dismantled by authorities. The Tor network, too, has been plagued by Denial of Service (DoS) attacks, as highlighted by the prolonged downtime of the renowned “Dread” forum. Operating a venture and seeking consistent revenue in such turbulent conditions is an immense challenge.
To counteract this instability, vendors on the dark web diversify their presence across various marketplaces and establish direct communication channels with their clientele. This strategy not only aids in resilience but also becomes an asset for Open Source Intelligence (OSINT) analysts. These communication channels, or “selectors,” can be used to trace the vendors across the internet, applying extensive knowledge, expertise, and resources. For instance, an email address obtained from a dark web site can often be linked to an identifiable internet presence through a search engine like Google.
Once we’ve tied the individual(s) to resources on the internet, we have numerous options to deanonymize them. Some of my favorite options include:
Uncovering Historical WHOIS Records
Examining historical WHOIS records can offer valuable insights into the registration details of a domain, shedding light on the website’s owner or operator. These records provide information that can be instrumental in investigations or research. Surprisingly, criminals may unknowingly disclose their identity or location by employing inadequate privacy protection measures, leading to inaccurate or incomplete WHOIS information.
Even if a website’s current WHOIS information is anonymized, it is often the case that at some point in the past, it was not. By delving into historical WHOIS records, it is possible to uncover gaps as short as four days where a site temporarily switched between private registration and revealing the true identity of its owner. These brief periods of disclosure can be crucial for discovering pertinent information about the website’s origins and the individuals behind it.
Understanding the historical context of WHOIS records can be a valuable tool in uncovering the true identities and activities associated with a particular website.
Unleashing the Power of OSINT on Forums
In the vast landscape of the internet, online forums serve as thriving communities where like-minded individuals congregate to discuss various topics. These forums not only provide a platform for exchanging ideas but also harbor a wealth of information that can be harnessed through Open Source Intelligence (OSINT) techniques. By delving into forums, OSINT practitioners can uncover valuable insights, gather intelligence, and gain a deeper understanding of diverse subjects. Let’s explore how OSINT can be effectively applied to extract meaningful data from forums.
The Rich Tapestry of Forum Data
Forums act as virtual gathering places where individuals engage in discussions, seek advice, share experiences, and express opinions. This dynamic environment generates a treasure trove of information waiting to be discovered. OSINT on forums involves carefully sifting through this data to extract relevant details that can contribute to investigations, research, or gaining a comprehensive understanding of a particular topic.
Extracting Valuable Insights
OSINT practitioners employ various techniques to extract valuable insights from forums. Here are some key strategies:
1. User Profiling: Analyzing user profiles can provide valuable information about individuals participating in the forum. Details like usernames, registration dates, post history, and shared personal information can offer insights into their interests, expertise, affiliations, or potential connections.
2. Content Analysis: Thoroughly examining forum threads, posts, and comments can reveal trends, patterns, and prevailing sentiments within the community. It can also help identify influential members, key discussions, or emerging topics that may be of interest.
3. Metadata Examination: Extracting metadata from forum content, such as timestamps, IP addresses, or geolocation data, can aid in tracking user activity, identifying potential aliases, or establishing connections between different forum participants.
4. Link Analysis: Forums often contain hyperlinks to external sources, websites, or social media profiles. Following these links can lead to a broader web of information, expanding the scope of OSINT investigations and providing additional context.
5. Reputation Assessment: Forums often employ reputation systems, such as likes, upvotes, or reputation points, to gauge the credibility and influence of users. Evaluating these reputation metrics can help prioritize information sources and identify trusted contributors.
Tools and Techniques for OSINT on Forums
A variety of tools and techniques can enhance the effectiveness of OSINT on forums:
1. Advanced Search Operators: Utilizing advanced search operators on search engines or within forum platforms can help narrow down specific threads, posts, or users of interest. By refining search queries, OSINT practitioners can focus their efforts on extracting the most relevant information.
2. Scraping and Data Extraction: Automated scraping tools enable the bulk collection of forum data, facilitating comprehensive analysis and efficient processing. However, it is crucial to adhere to ethical and legal guidelines while using such tools.
3. Data Visualization: Visualizing forum data using graphs, charts, or network analysis techniques can reveal connections, clusters, or patterns that might not be immediately apparent. This visual representation aids in understanding complex relationships within the forum ecosystem.
4. Monitoring and Alerting: Setting up automated monitoring and alert systems for specific keywords, usernames, or topics can provide real-time updates on relevant discussions or new information posted on forums. This proactive approach ensures timely access to valuable intelligence.
Ethical Considerations and Privacy
While conducting OSINT on forums, it is essential to prioritize ethical practices and respect user privacy. OSINT practitioners should adhere to legal boundaries, terms of service, and guidelines set by forum platforms. Respecting user privacy, avoiding personal attacks, and refraining from engaging in any illegal activities are paramount.
Unveiling the Shadows: Using Breach Data-Based OSINT to Identify Members of the Deep Web
Breach data, resulting from large-scale data breaches and leaks, has become a valuable resource for OSINT practitioners. These breaches expose vast amounts of personal information, including usernames, email addresses, passwords, and even IP addresses. By analyzing this breach data, OSINT practitioners can establish connections between individuals operating on the Deep Web and their real-world identities.
Uncovering Identities through Breach Data-Based OSINT
Here are some ways breach data-based OSINT can be used to identify members of the Deep Web:
1. Email Address Analysis: Email addresses are often used as identifiers across various online platforms. By cross-referencing email addresses found in breach data with those associated with Deep Web activities, OSINT practitioners can link individuals to their online personas.
2. Username Mapping: Many Deep Web users employ consistent or similar usernames across different platforms. By analyzing breach data and mapping usernames to Deep Web activities, OSINT practitioners can unveil the true identities of individuals operating within this hidden realm.
3. Password Reuse: Password reuse is a common practice among internet users. Analyzing breach data for reused passwords can provide insights into other online accounts or platforms used by individuals on the Deep Web, potentially exposing their real-world identities.
4. IP Address Tracking: IP addresses captured in breach data can be compared to those associated with Deep Web activities. This analysis can help identify individuals who have inadvertently revealed their true IP address while operating within the Deep Web.
5. Social Media Connections: Breach data often contains social media account information. By correlating this data with Deep Web activities, OSINT practitioners can uncover connections between individuals operating anonymously on the Deep Web and their publicly known social media accounts.
Ethical Considerations and Legal Boundaries
It is essential to approach breach data-based OSINT with a strong sense of ethics and respect for privacy. OSINT practitioners must adhere to legal boundaries, ensuring that their activities remain within the confines of the law. Respecting user privacy, avoiding personal attacks, and refraining from engaging in any illegal activities are paramount in conducting breach data-based OSINT.
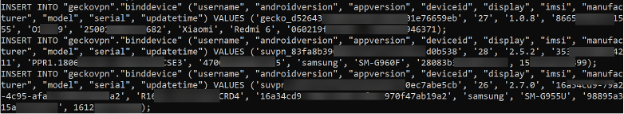
An example of a leak that has proven helpful for some investigators was the 2021/2022 leak of 10GB of data from several VPN providers, including SuperVPN, GeckoVPN, and ChatVPN. This data contained full names, billing details, and potentially unique identifiers about the devices used, including the IMSI of mobile devices.
Unmasking the Dark Web: Harnessing AI to Reveal the True Identity of Websites
The Dark Web, a hidden corner of the internet notorious for illicit activities, thrives on anonymity and secrecy. Uncovering the true identity of Dark Web websites has traditionally been a challenging task. However, with the advent of Artificial Intelligence (AI) and advanced techniques, it is now possible to utilize AI to unravel the hidden identities of these websites. In this article, we will explore how AI can be leveraged to unmask the true identity of Dark Web websites.
Understanding the Dark Web
Before diving into the role of AI, it is crucial to comprehend the nature of the Dark Web. The Dark Web refers to a part of the internet that exists on encrypted networks, such as Tor, and is intentionally hidden from search engines. It provides a platform for various illegal activities, including the sale of drugs, weapons, stolen data, and other illicit services.
AI-Powered Techniques for Unmasking Dark Web Websites
Here are some ways AI can be utilized to uncover the true identity of Dark Web websites:
1. Natural Language Processing (NLP): NLP techniques can be employed to analyze the content and language used on Dark Web websites. By studying linguistic patterns, sentiment analysis, and text classification, AI algorithms can identify similarities or connections between different websites. This analysis can help reveal the true identity or affiliations of these websites.
2. Image and Video Analysis: Dark Web marketplaces often use images and videos to showcase their products or services. AI-powered image and video analysis techniques can be employed to extract information from these multimedia files. By comparing and matching visual elements, AI algorithms can uncover similarities between different websites, potentially exposing their true identities.
3. Network Traffic Analysis: AI can be utilized to analyze network traffic patterns associated with Dark Web websites. By monitoring and analyzing the flow of data, AI algorithms can identify patterns, connections, or anomalies that may lead to the discovery of the true identity of these websites.
4. Machine Learning and Anomaly Detection: Machine learning algorithms can be trained on large datasets of known Dark Web websites to learn patterns and characteristics specific to these underground platforms. By leveraging anomaly detection techniques, AI algorithms can identify websites that deviate from normal patterns, potentially indicating hidden identities or affiliations.
5. Link Analysis: AI-powered link analysis techniques can be employed to examine the relationships between Dark Web websites. By analyzing hyperlinks, references, and connections, AI algorithms can uncover hidden networks and expose the true identity of websites by tracing back to their sources.
Ethical Considerations and Legal Boundaries
When using AI to unmask Dark Web websites, it is crucial to adhere to ethical considerations and legal boundaries. Respect for privacy, compliance with applicable laws, and avoiding engagement in any illegal activities are of utmost importance. It is essential to use AI techniques responsibly and ensure that the methods employed do not violate any legal or ethical standards.
Conclusion
Artificial Intelligence presents a powerful tool in the quest to uncover the true identity of Dark Web websites. Through techniques such as natural language processing, image and video analysis, network traffic analysis, machine learning, anomaly detection, and link analysis, AI algorithms can reveal hidden connections and patterns. However, it is essential to approach this process ethically, respecting privacy and adhering to legal boundaries.
As AI continues to advance, it holds the potential to shed light on the previously impenetrable Dark Web, contributing to efforts aimed at combating illegal activities and ensuring a safer online environment.
