Defend Your Business Against the Latest Cyber Threats
Info Security Solution is a cutting-edge cybersecurity company certified under ISO 27001:2022 and ISO 20000-1 standards. We specialize in risk assessment and strategic consulting to mitigate digital and social security threats. Our services encompass comprehensive audits of networks, applications, and systems, conducted by a team of highly qualified professionals, including Certified Ethical Hackers (CEH), Computer Hacking Forensic Investigators (CHFI), EC-Council Certified Security Analysts (ECSA), ISO 27001 Lead Auditors, GDPR and MITRE specialists, and CERT-IN-approved Security Auditors.
Chat With Us+
Worldwideclients
+
Cyber SecurityExperts
%
Retentionrate
Effective Approach for Your Cyber Security
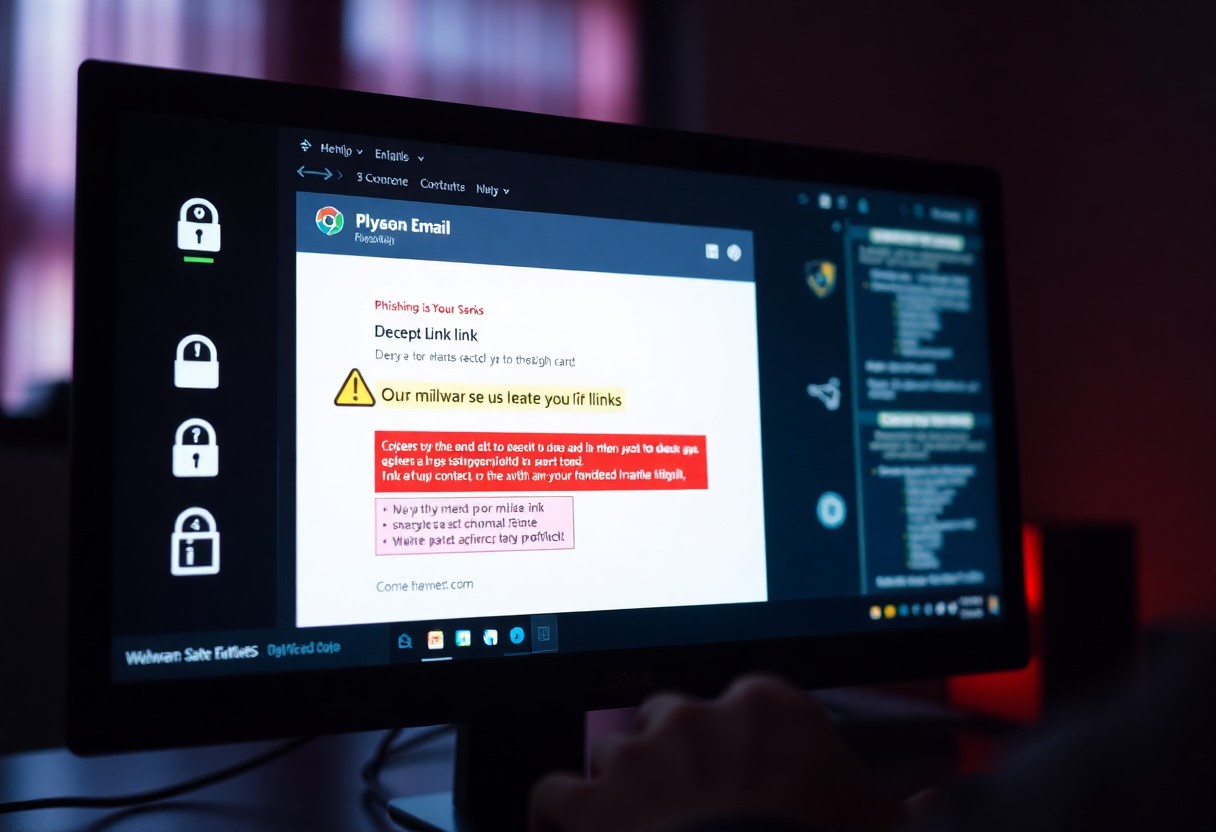
Increased & Evolving Threat
Facing an ever-growing and evolving landscape of cyber threats, staying ahead requires constant vigilance and adaptive security measures
Learn MoreContinuous Monitoring
Continuous monitoring is the bedrock of real-time security, providing an unblinking eye over your digital assets to swiftly detect and respond to threats
Learn MoreStructural Weaknesses
Structural weaknesses in cybersecurity is a critical entry points for attackers, leading to devastating breaches and compromise of sensitive data
Learn MoreWidening Attack Surface
The expansion of attack surfaces, compounded by the rise of shadow IT, significantly increases the complexity and potential for security incidents
Learn More
Robust Assessment for Data Breach Preparedness and Ransomware Resilience
Fortify your cyber resilience with our in-depth Data Breach and Ransomware Readiness Assessment. Discover and strengthen your vulnerabilities before they're exploited
- Threat Simulations
- Identify Insider Threat
- Compliance Checks
- Security Controls Scrutiny
- Identify Paste site leaks
- Lookalike Doman Check
- Shadow IT Assessment
- Deep/Dark Web Data Leak
- EICAR Assessment
- Subdomain Takeover
- Domain / IP Reputation Checking
Want Your Very Own Cyber Range ?
We Are the ONLY Cyber Range Consultants In India

Customizable Attack Playground: Execute Any Attack With Ease
Test on a custom-built cyber range designed for your specific needs. Explore over 70,000 exploits and 500+ device enumeration methods across IT and OT environments.
Best for Attack Scenario Testing
Simulate Real-World Attacks: ICS & IT vulnerability library
Our extensive protocol library lets you explore IT and ICS vulnerabilities in a safe, emulated, and controlled environment with over 1000+ malware & Ransomware variants.
Not only IT, but full threat coverage
MISP, InfectionMonkey, Caldera and many more
MISP, InfectionMonkey, Caldera, and more, integrate seamlessly to enhance your cyber range experience and help you design intricate attack scenarios for hands-on experiences.
Own a Platform - Multiple Integrations360 Degree Protection For Your Oragnization
By Following 3 Steps


Result with Mitigation Support
Receive detailed vulnerability insights paired with expert support
Step Three